Description of your personal account
General description
The MULTIFACTOR administrator's personal account is necessary in order to manage your resources, users and their groups.
This short guide will help you understand the functionality and reveal all the options for managing the multi-factor authentication service.
##Entrance You can register by clicking on the appropriate hyperlink
Login is available by login/password, as well as through mail.ru email or your Google account. If you lose your password, you can recover it yourself in the login window. If it is impossible to confirm 2FA, for example, replacing a phone, please contact support@multifactor.kz with a request to reset the 2FA confirmation method
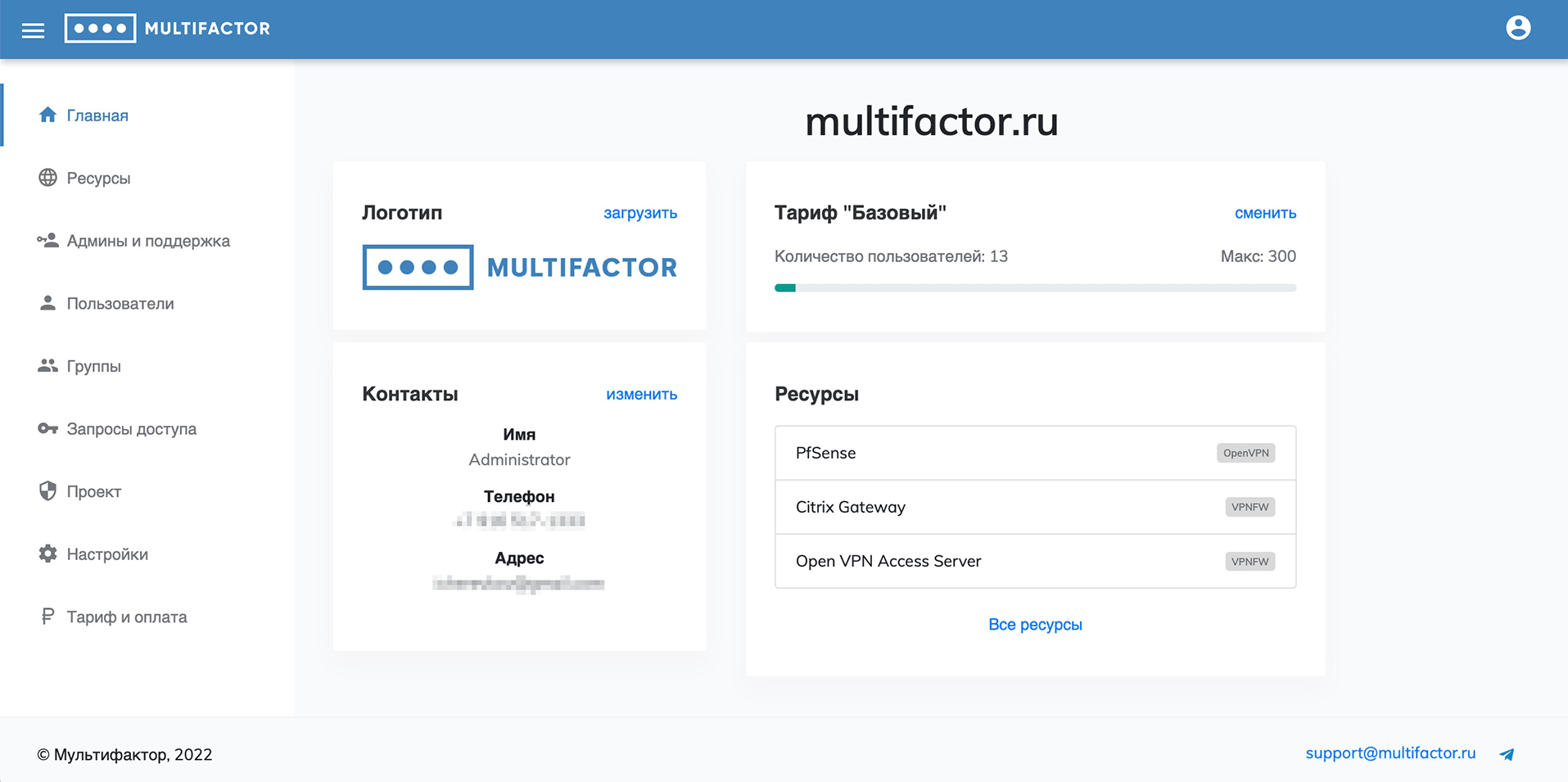
Home
The main page provides a brief summary of the project.
Changing the logo on the main page of your account will allow you to personalize the web application login page for your users.
Contacts on the main page of your Personal Account will be displayed to your users in case of problems using the service. You can provide both a phone number and an email.
Resources
This section manages your information resources and multi-factor authentication systems.
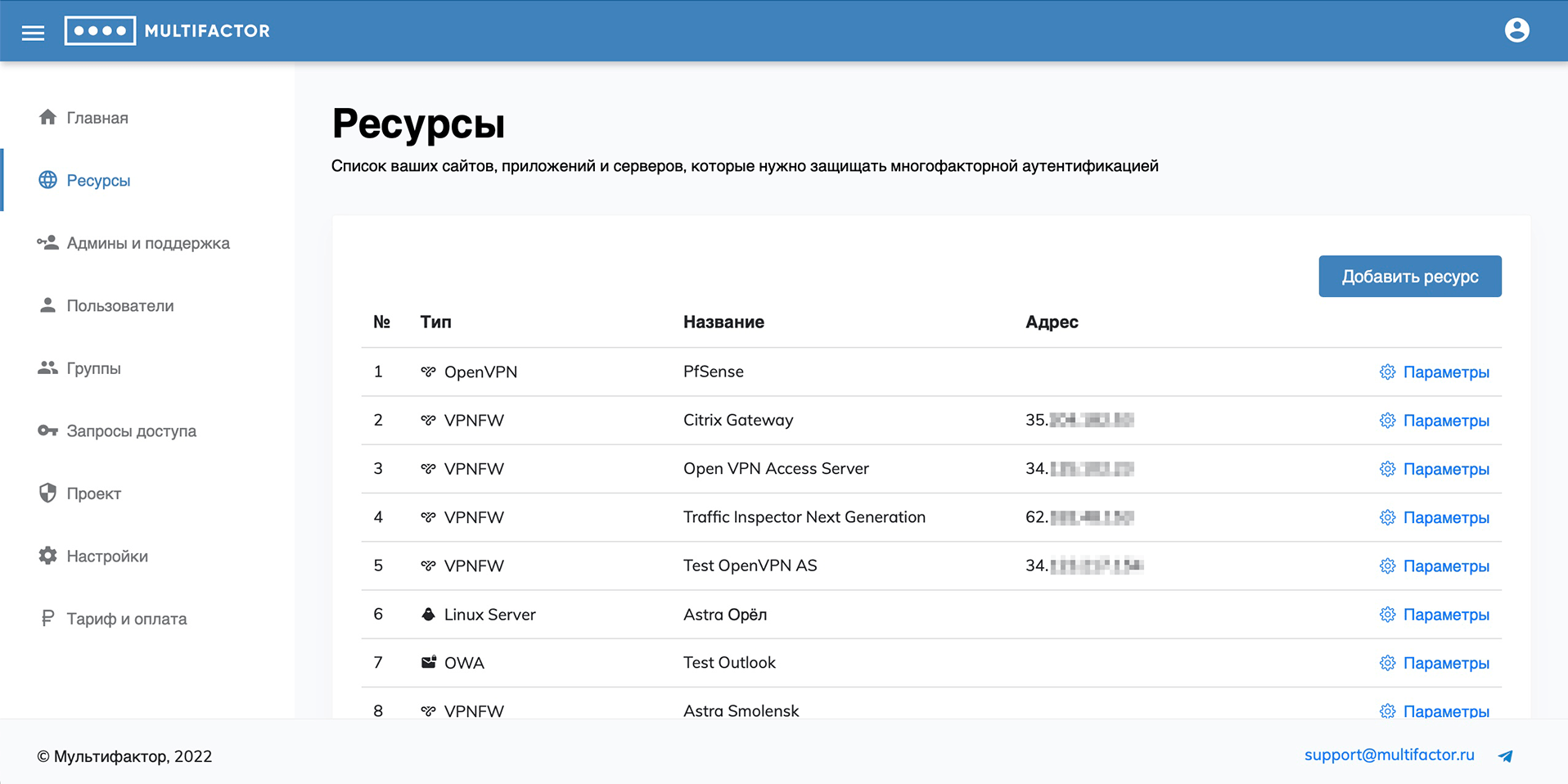
There are 4 types of resources available for adding: “Site”, “Firewall”, “OS/Server” and “Other”.
-
To work with the “Site” resource type, the following solutions are presented:
- Website;
- Self-Service portal;
- SAML application;
- OAuth / OpenID application;
- Yandex.Cloud;
- Outlook Web Access.
Work with "Website" resources is carried out through API, and API Key and API Secret are used for authentication.
Work with "SAML" resources is carried out using the SAML protocol; mutual trust is established between the resource and the Multifactor by exchanging public certificates.
Work with "OAuth / OpenID" resources is carried out using the OAuth protocol, Client ID and Client Secret are used for authentication.
-
To work with the “Firewall” resource type:
If your network equipment is not listed, use the "Other" resource type, which is generic.
-
To work with the “OS/Server” resource type:
- Linux;
- Windows;
- OpenVPN;
- Windows Remote Access and VPN;
- Windows RD Gateway;
- Windows Network Policy;
- VMware Horizon;
- Citrix Gateway.
For resources of this type, the work is built using Radius server, for authentication it requires the NAS-Identifier and Shared Secret parameters.
-
The “Other” resource type includes:
Resources of the "LDAP application" type use LDAP Proxy component, and for authentication it requires the NAS-Identifier and Shared Secret parameters.
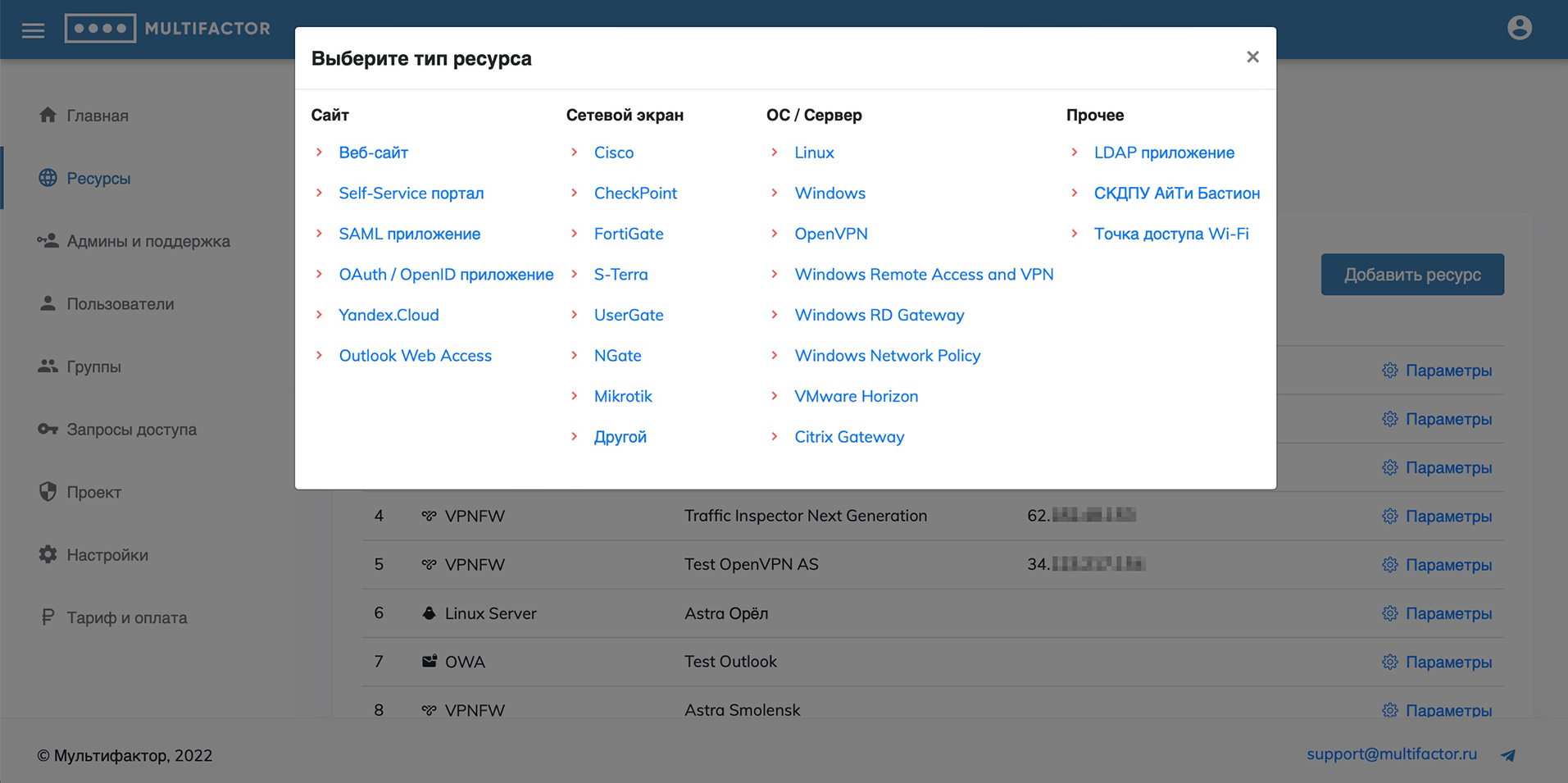
You can add the type of resource you need, and in the settings section, view the authentication data and edit the name or address of the resource.
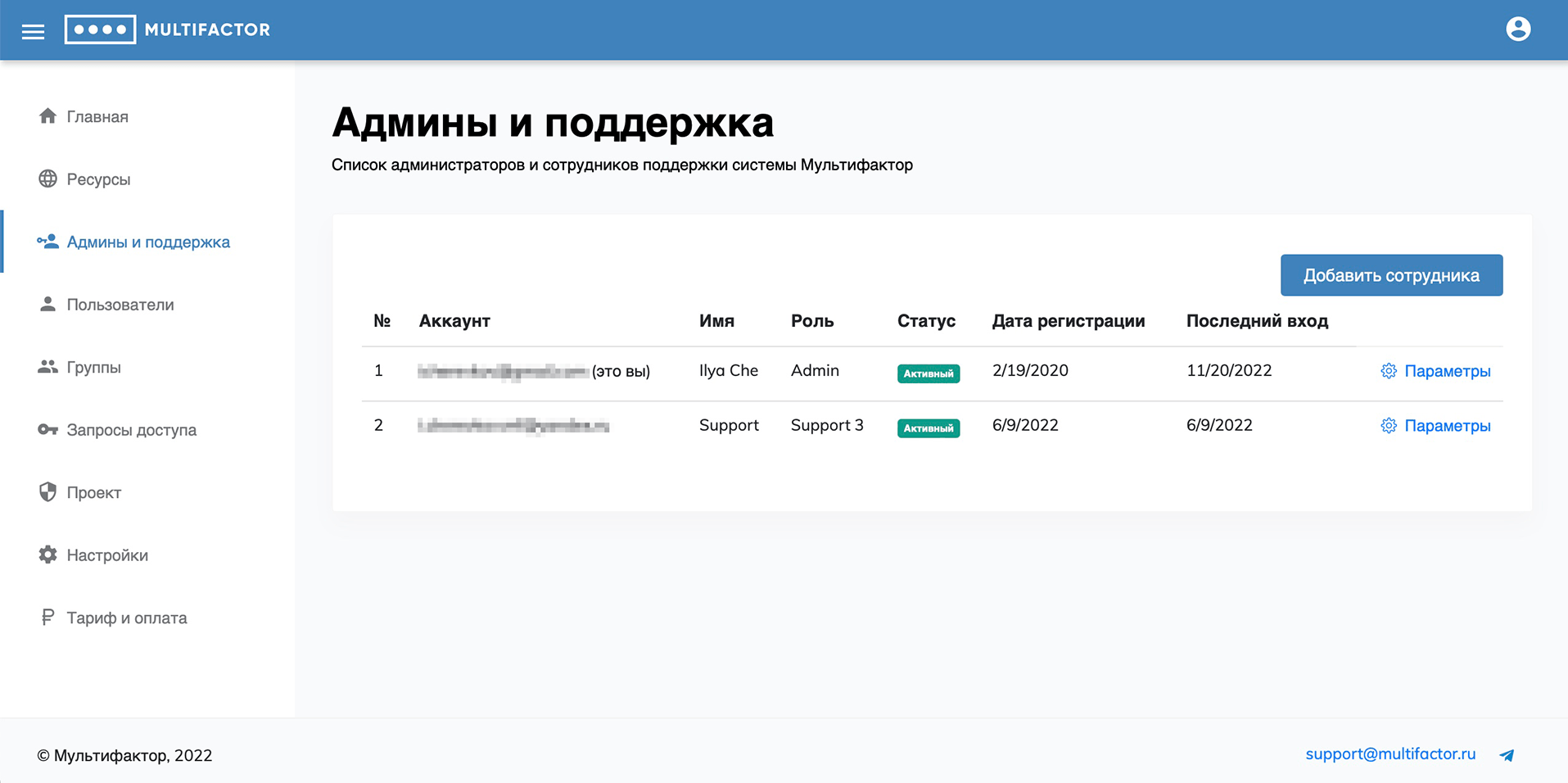
Admins and support
This section manages the administrators of your system. A role-based access system is provided. Roles:
- Admin: all powers;
- Support 1: read-only access to the "Users" and "Access Requests" sections;
- Support 2: access to the “Users” and “Access Requests” sections with the ability to send a link to configure the second factor and disable user authentication methods;
- Support 3: access to the "Users" and "Access Requests" sections, full user management except for import and export.
- Support 4: Includes all the powers of Support 3 with the ability to let users through without authentication.
When added, the administrator will receive a link for the first login, upon clicking which he will be able to set a password and configure multi-factor authentication.
Any administrator except yourself can be blocked.
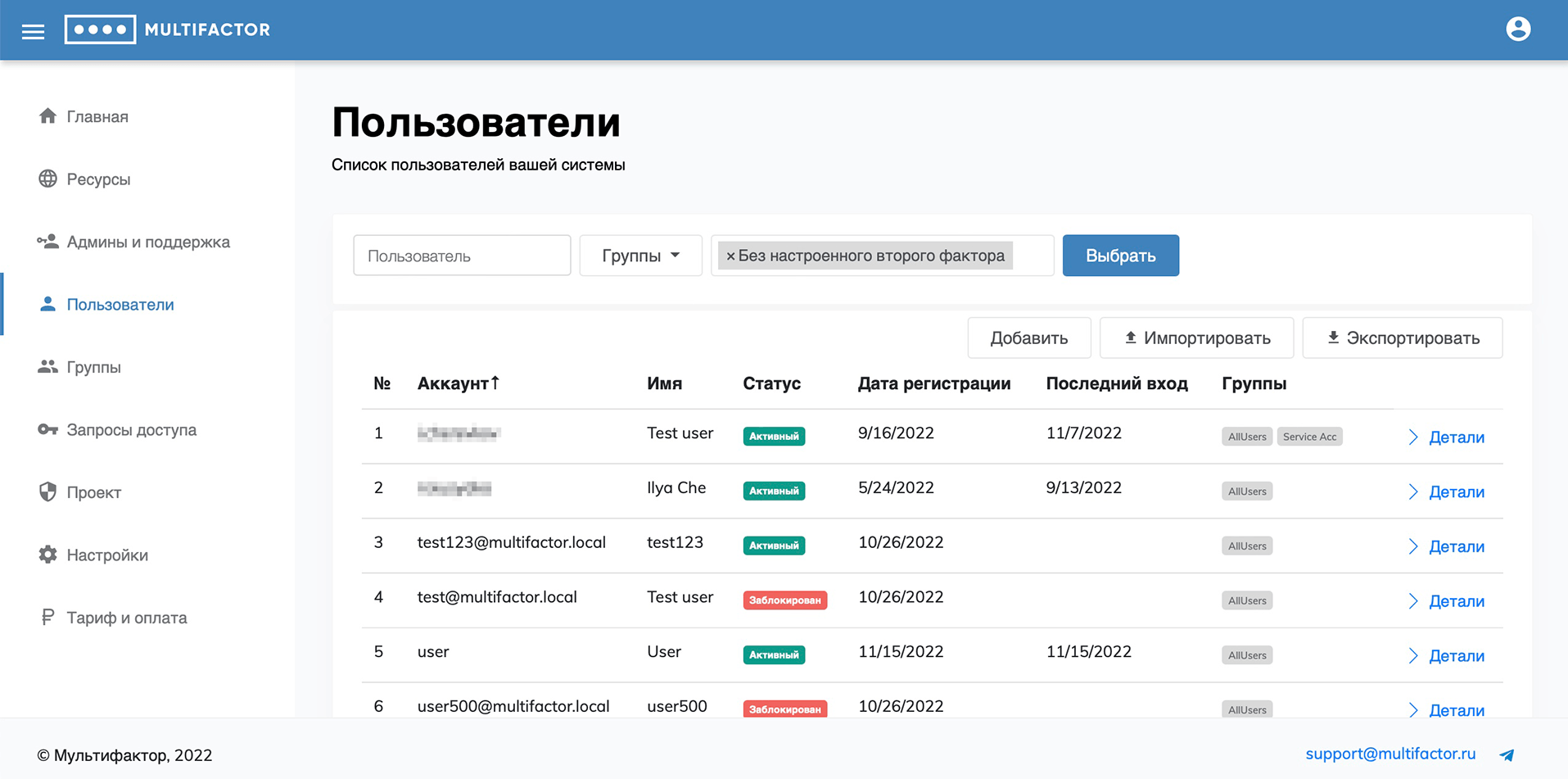
Users
This section displays your users.
By default, all your users that you have directed to two-factor authentication are added here, but you can add a user manually or bulk import users from a CSV or TXT file.
When adding a user, you can specify his name and login in the system, configure his membership in a particular user group. In this case, automatically created users fall into the All Users system group.
For users without an explicitly specified name, we pull the name from Telegram if they have enabled this authentication method.
It is possible to filter users by name, groups and additional filters:
- Blocked;
- Without configured second factor;
- Without e-mail;
- Never connected;
- Haven't connected for more than 30 days.
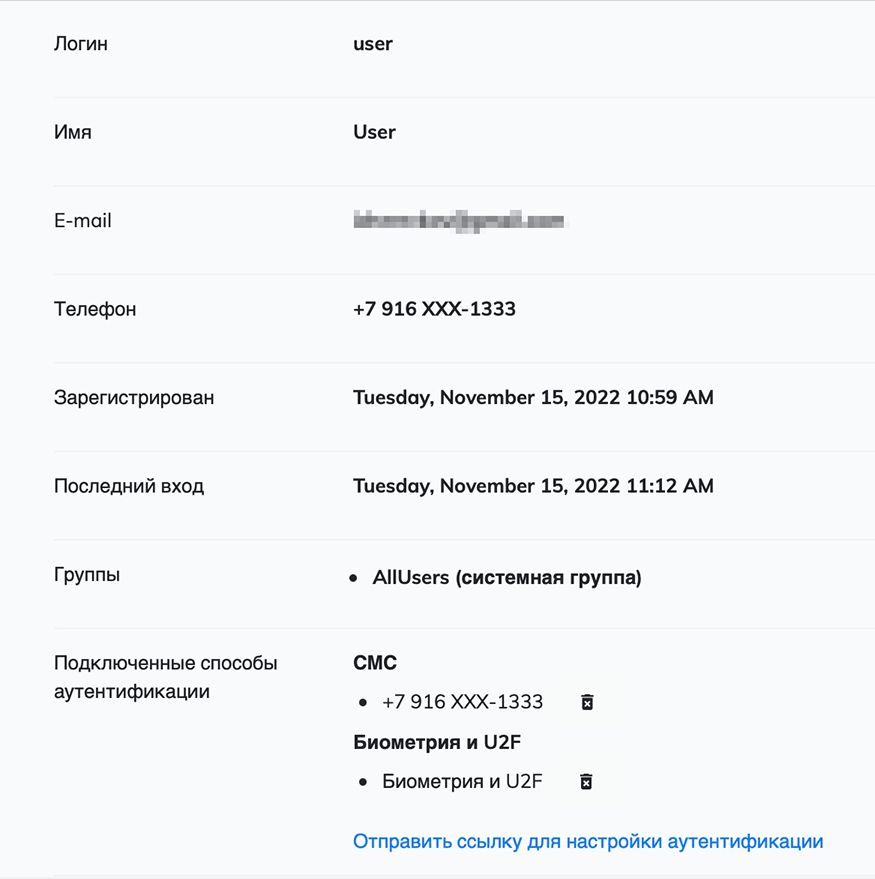
When viewing a user, you can find out his registration details, last login, status and access settings, and configured authentication methods. A user can be blocked or deleted if you do not want them to authenticate with Multifactor. You can also change user profile information and unlink configured authentication methods.
You can send the user a link to set up authentication if for some reason they have not previously enabled multi-factor authentication.
The actual configuration of user access is done by editing access for groups.
User statuses:
- Active - the user has registered and enabled 2FA
- Invitation sent - user is waiting for 2FA connection
- Blocked - the user is blocked by the project administrator
- Temporarily blocked - user is temporarily blocked after several unsuccessful login attempts
- Suspended - user is suspended due to insufficient number of licenses in the project
Groups
By default, you have access to one system access group, All Users. It includes new users created automatically.
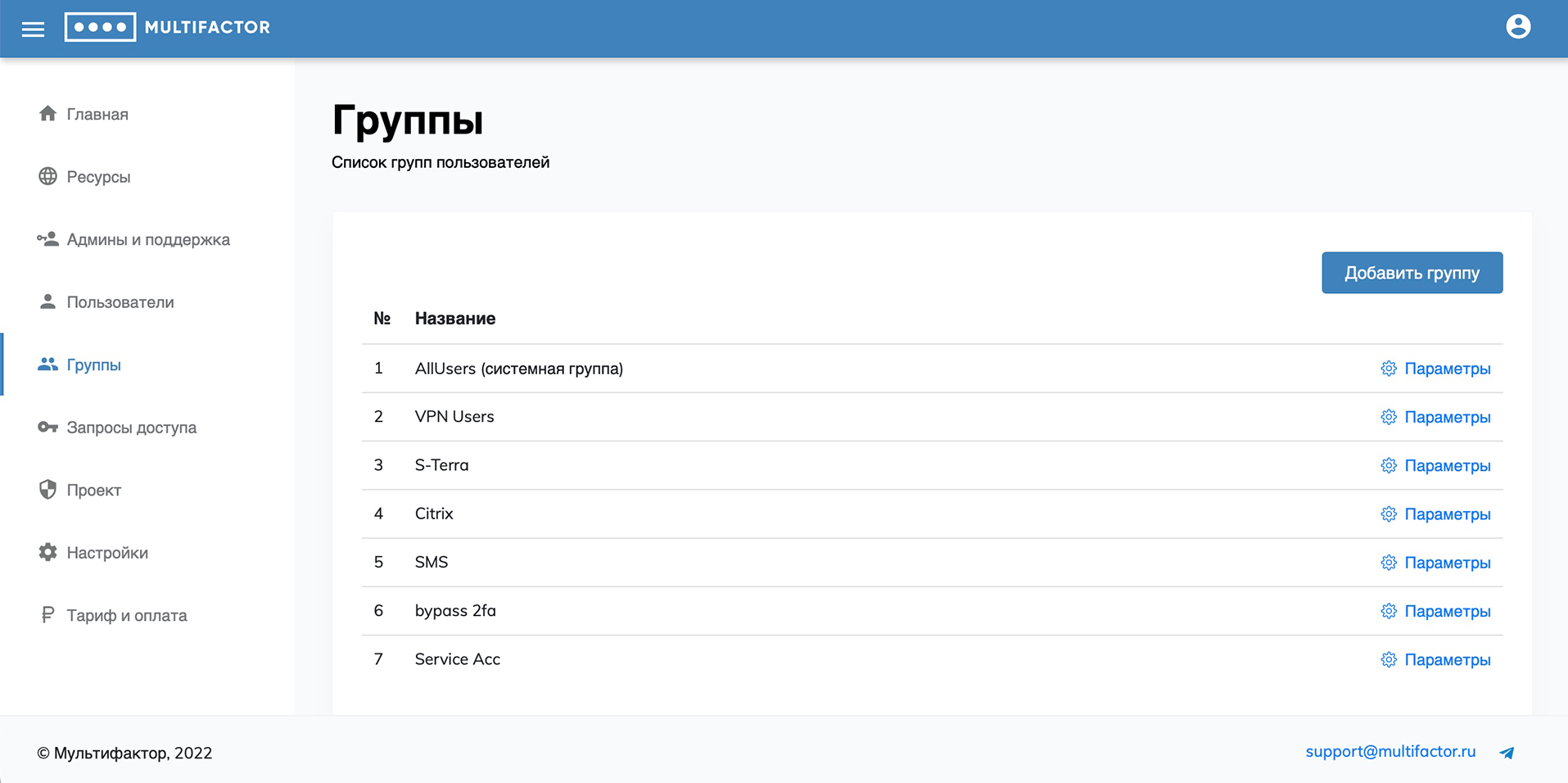
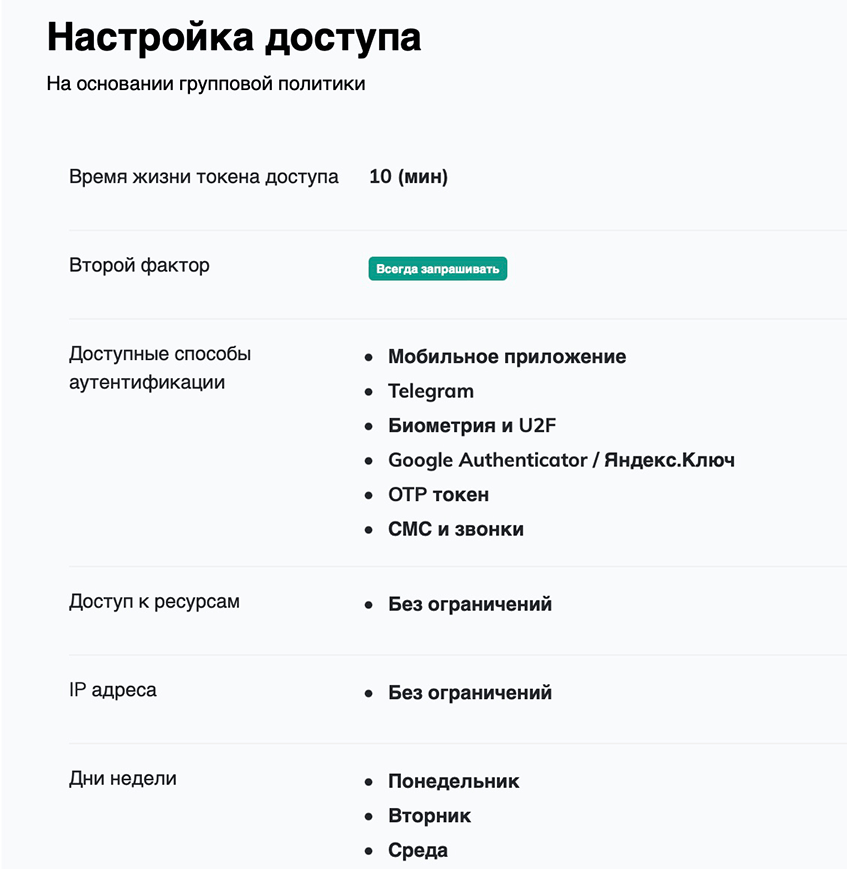
When creating and editing a group, you can specify:
- name of the group;
- lifetime of the access token;
- in what case to request the second factor;
- authentication methods available to users of this group (don’t forget to leave at least one available);
- resources to which the group has access;
- IP addresses or subnets from which connection to resources is allowed;
- days of the week on which access is allowed for this user group.
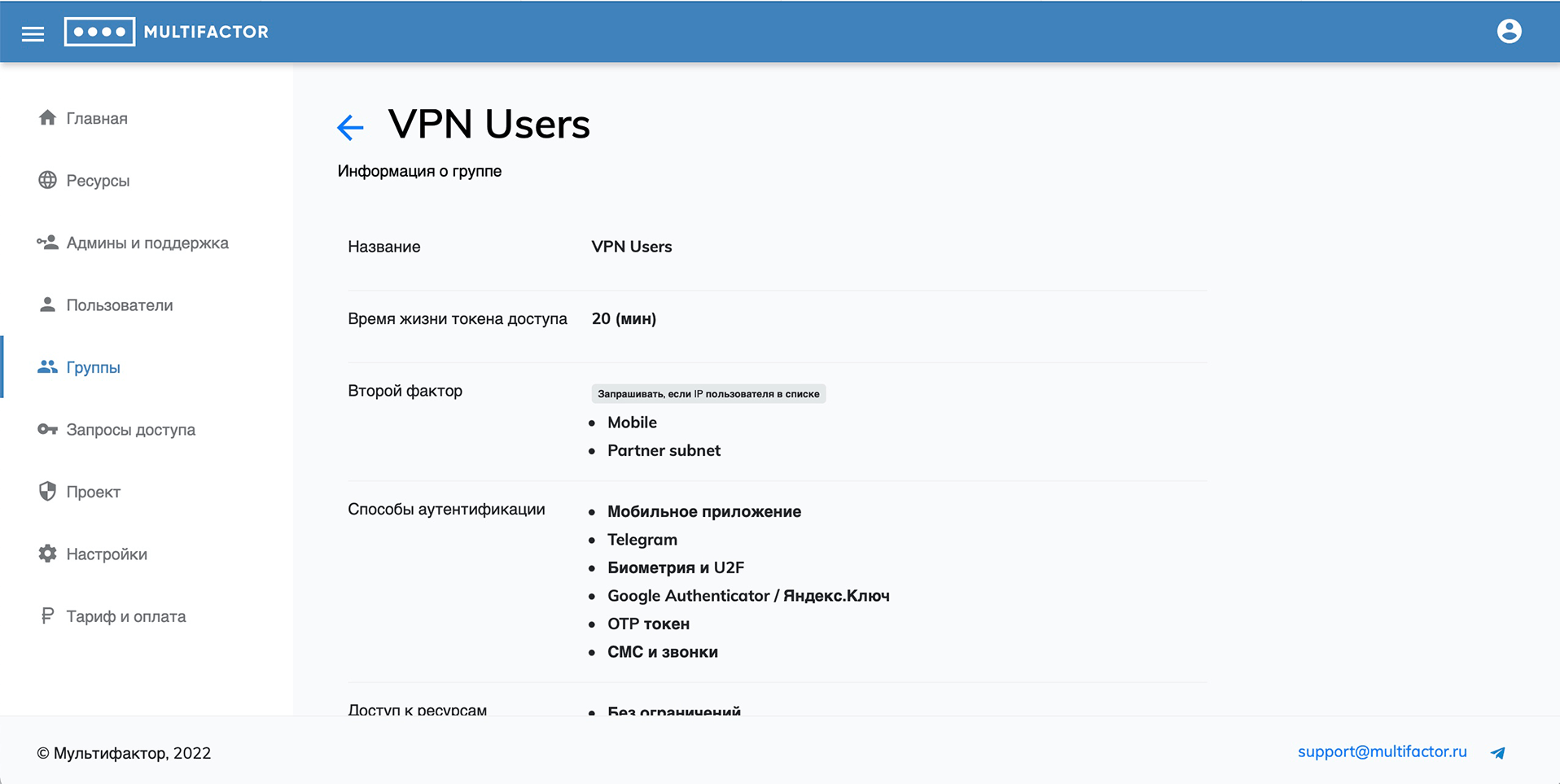
Unconditional and conditional second factor query
There are 2 options for the second factor query logic:
-
Unconditional
- Always ask;
- Never ask;

-
Conditional
- Request if the user's IP is on the list (black list);
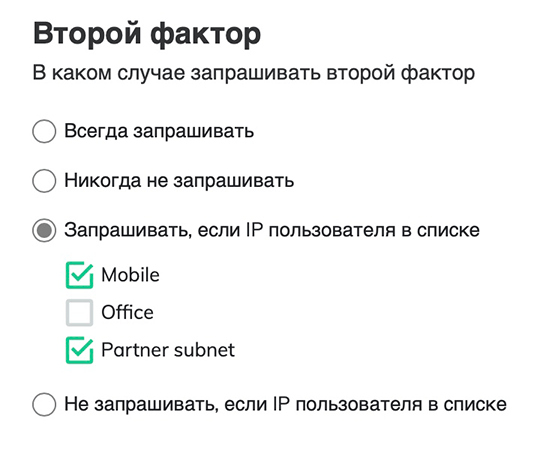
- Do not request if the user's IP is on the list (white list).
The last two modes “Prompt if the user’s IP is on the list” and “Do not request if the user’s IP is on the list” represent the black and white lists, respectively. IP ranges are pre-configured in the "Settings" -> "IP Ranges" section.
- Request if the user's IP is on the list (black list);
When calculating the final policy, the settings of all groups in which the user is located are taken into account - the system "AllUsers" and user groups.
- when using unconditional logic in user groups, settings in user groups have higher priority than in the AllUsers system group. At the same time, “Never prompt” is higher in priority than “Always prompt”;
- when using different logics (conditional/unconditional) in user groups, conditional logic is always higher in priority than unconditional;
- logic with a black list (“Request if the user’s IP is on the list”) takes precedence over logic with a white list (“Do not request if the user��’s IP is on the list”).
The resulting second factor request and resource access policy for each user can be checked in the user details.
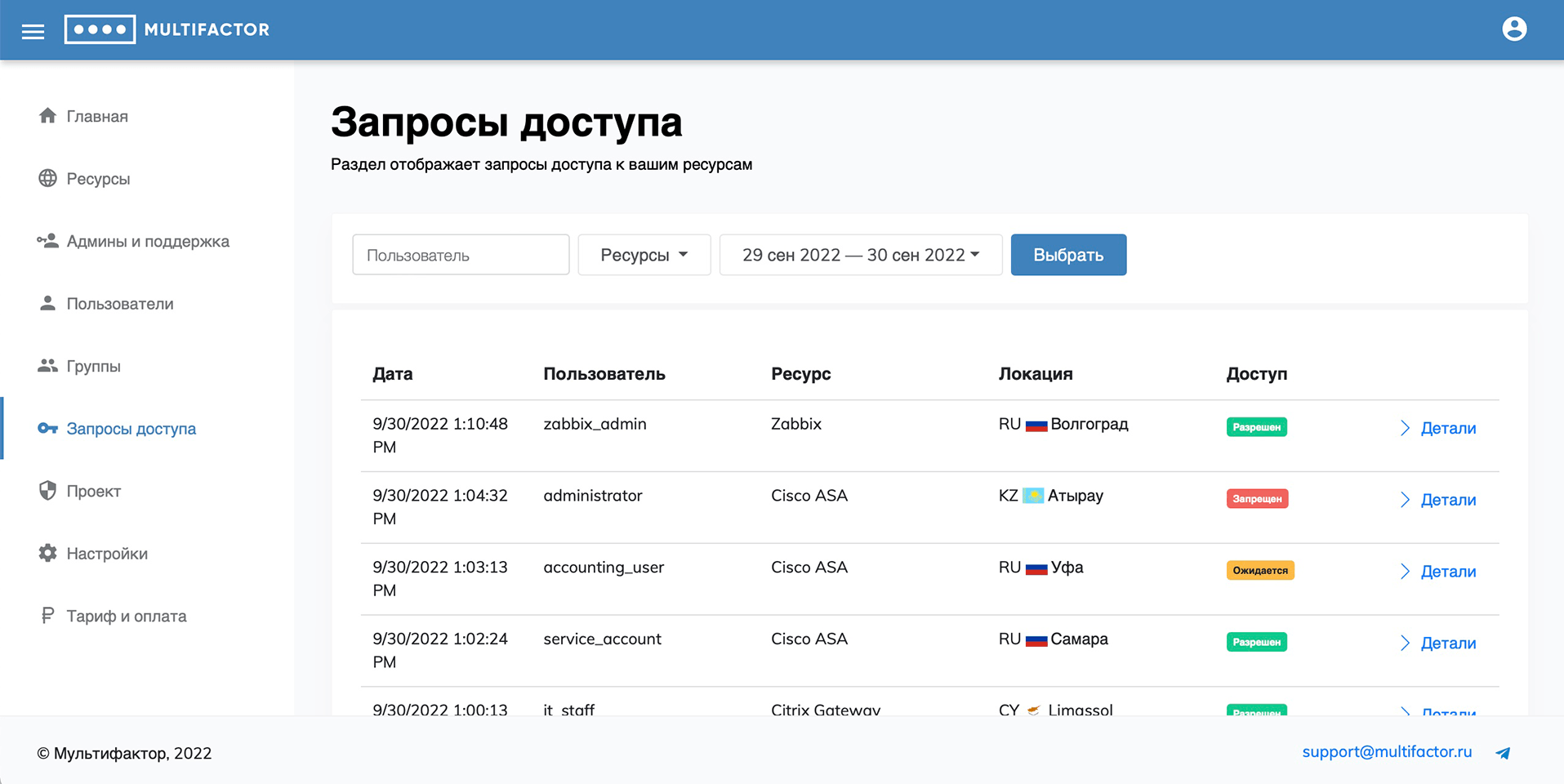
Access requests
In this section, the system administrator sees all access requests of his users.
You can use a filter to conveniently track a specific user's access to the resources you are interested in. Including for a certain period of time.
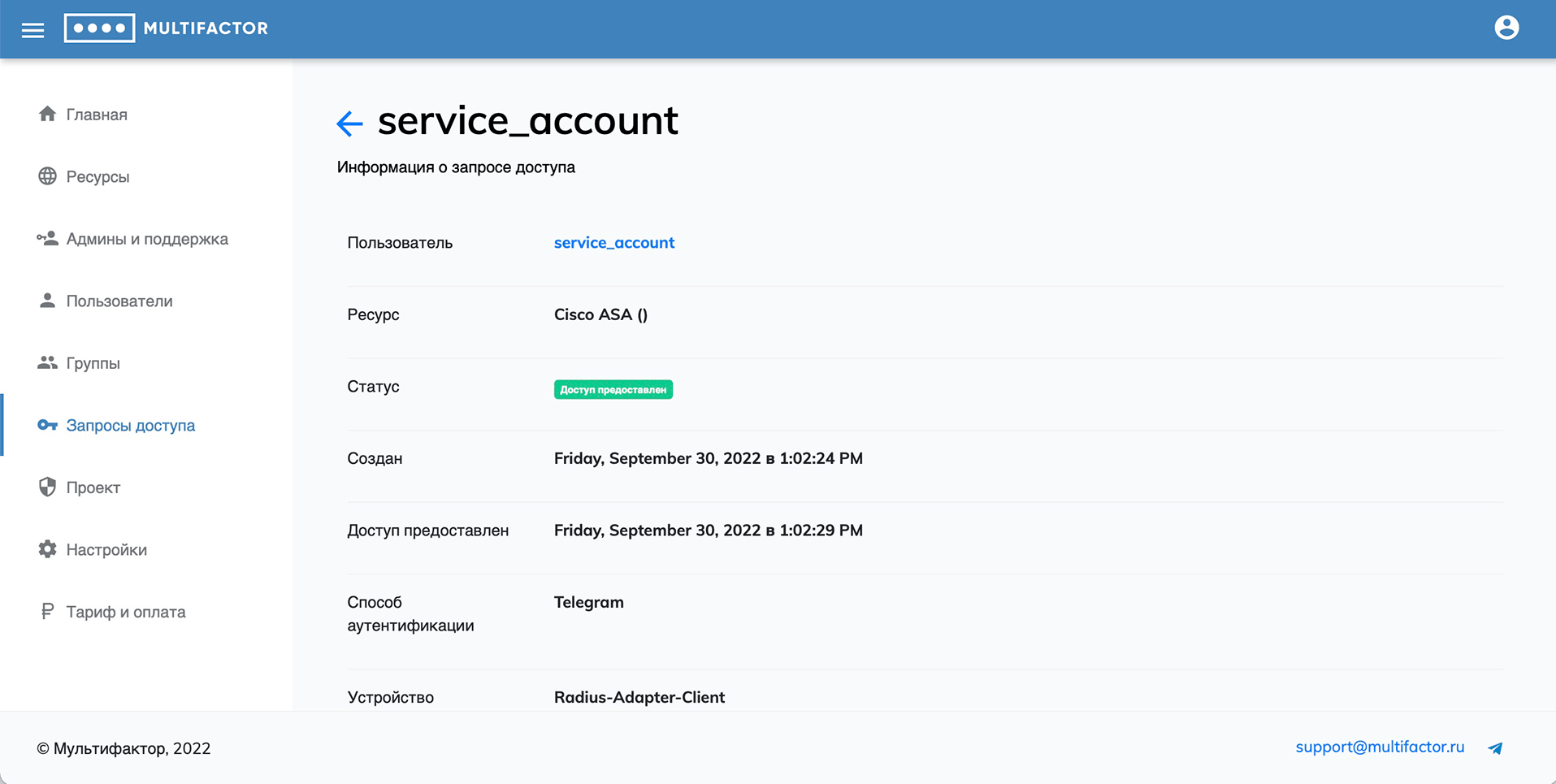
In the detailed information about the access request, you can find the following information:
- the resource to which the user gained access;
- what authentication method was chosen;
- at what time the authorization request arrived;
- fingerprint of the device from which the request was made;
- IP address and geolocation.
The administrator can allow a user to pass without authorization. To do this, go to the details of the request with the status “Authentication Awaiting” and click on the “Pass without authentication” button. This method will only work if the token has not yet expired and the user has not left the authentication screen.
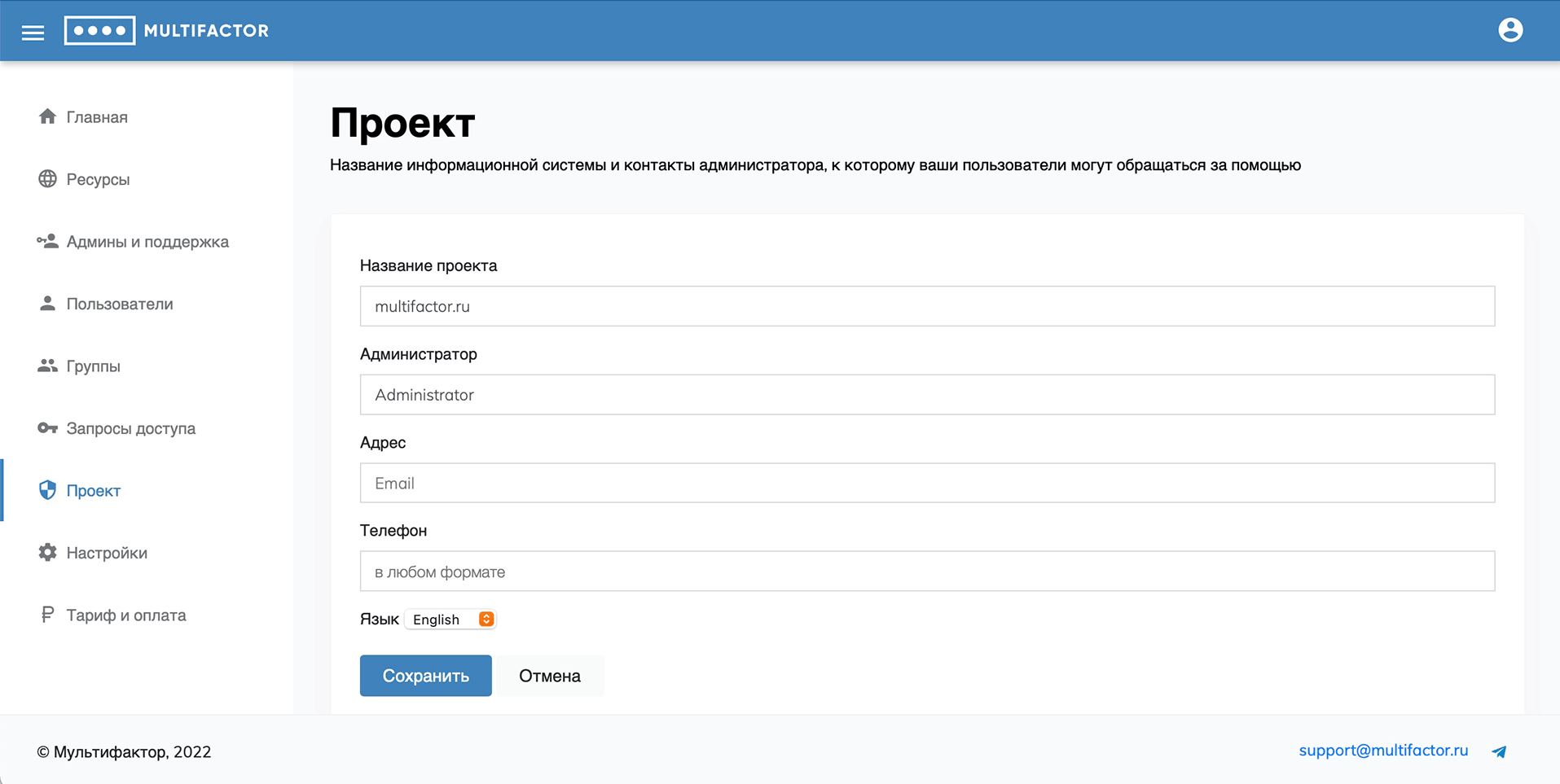
Project
In this section, you can set a profile description: the name of the information system and the contacts of the administrator to whom your users can contact for help.
Settings
The section contains 6 tabs that you can customize to suit your needs: Accounts, SMS, Calls, Advanced API, Account Providers, IP Ranges.
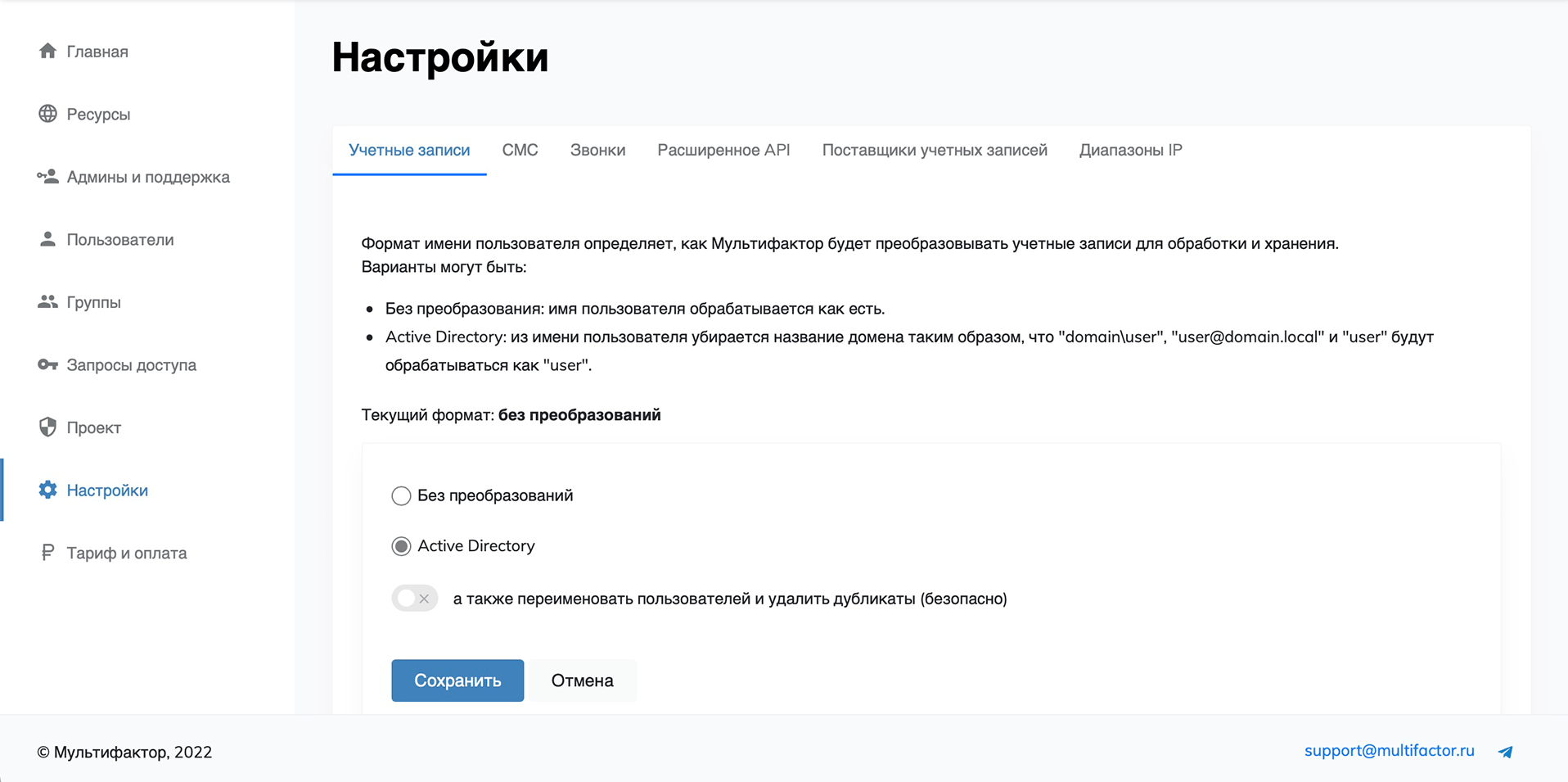
Accounts
The username format determines how MULTIFACTOR will convert accounts for processing and storage.
Options could be:
-
No conversion: The username is treated as is.
-
Active Directory: Removes the domain name from the username so that "domain\user", "user@domain.local" and "user" will be treated as "user".
In the section there is a switch "as well as rename users and remove duplicates (safely)" to rename existing ones. Renaming logic:
- If there is more than 1 UZ format for one user in the system (domain\user, user, user@domain), then one record is selected according to the criteria:
- with linked 2fa
- with the last entry date
- Next, this record is converted into Active Directory format (only login - user), other formats are deleted.
- If there is more than 1 UZ format for one user in the system (domain\user, user, user@domain), then one record is selected according to the criteria:
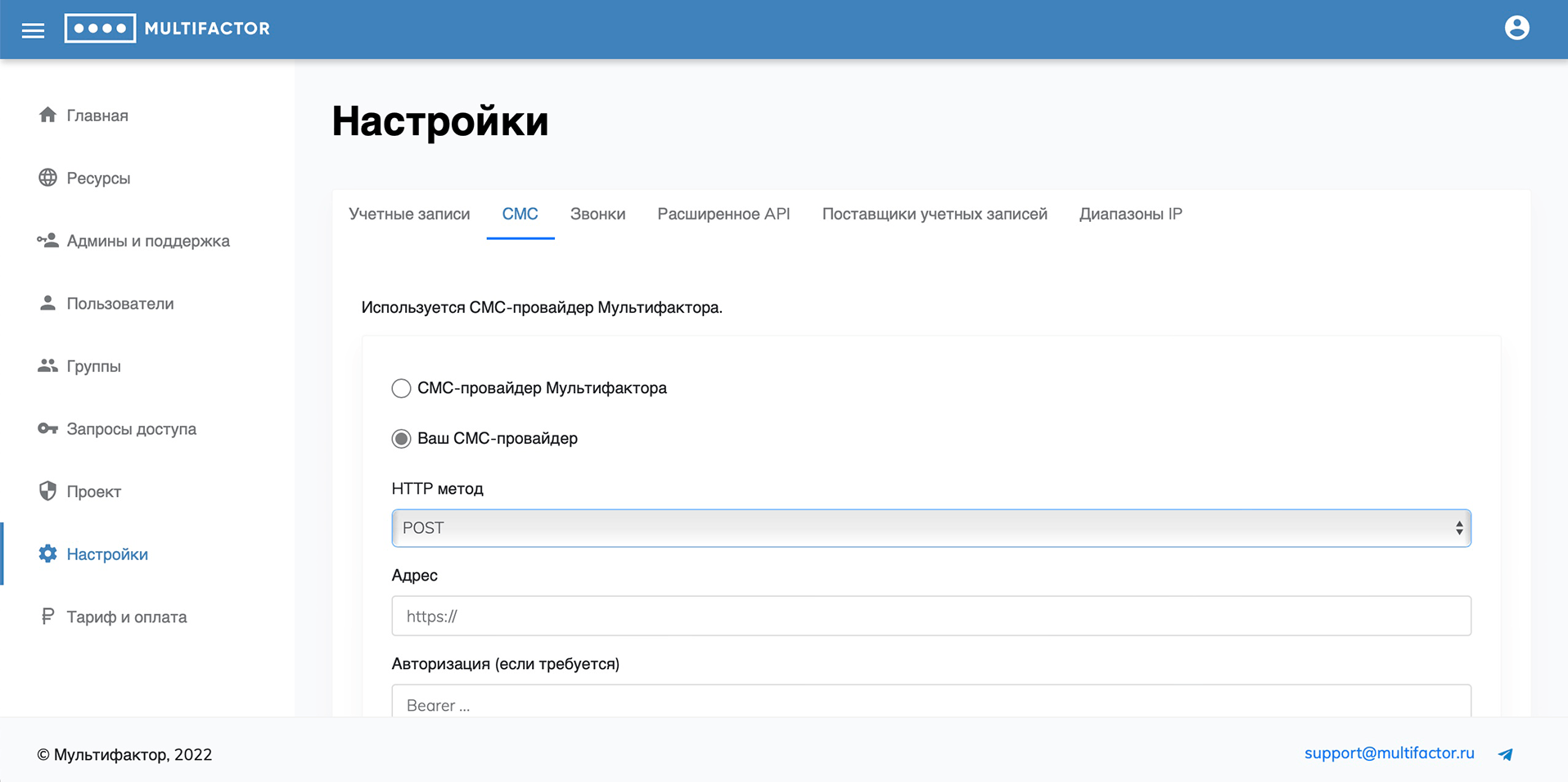
SMS
By default, the Multifactor SMS gateway is used.
It is possible to integrate your own SMS gateway using the HTTP protocol (GET, POST).
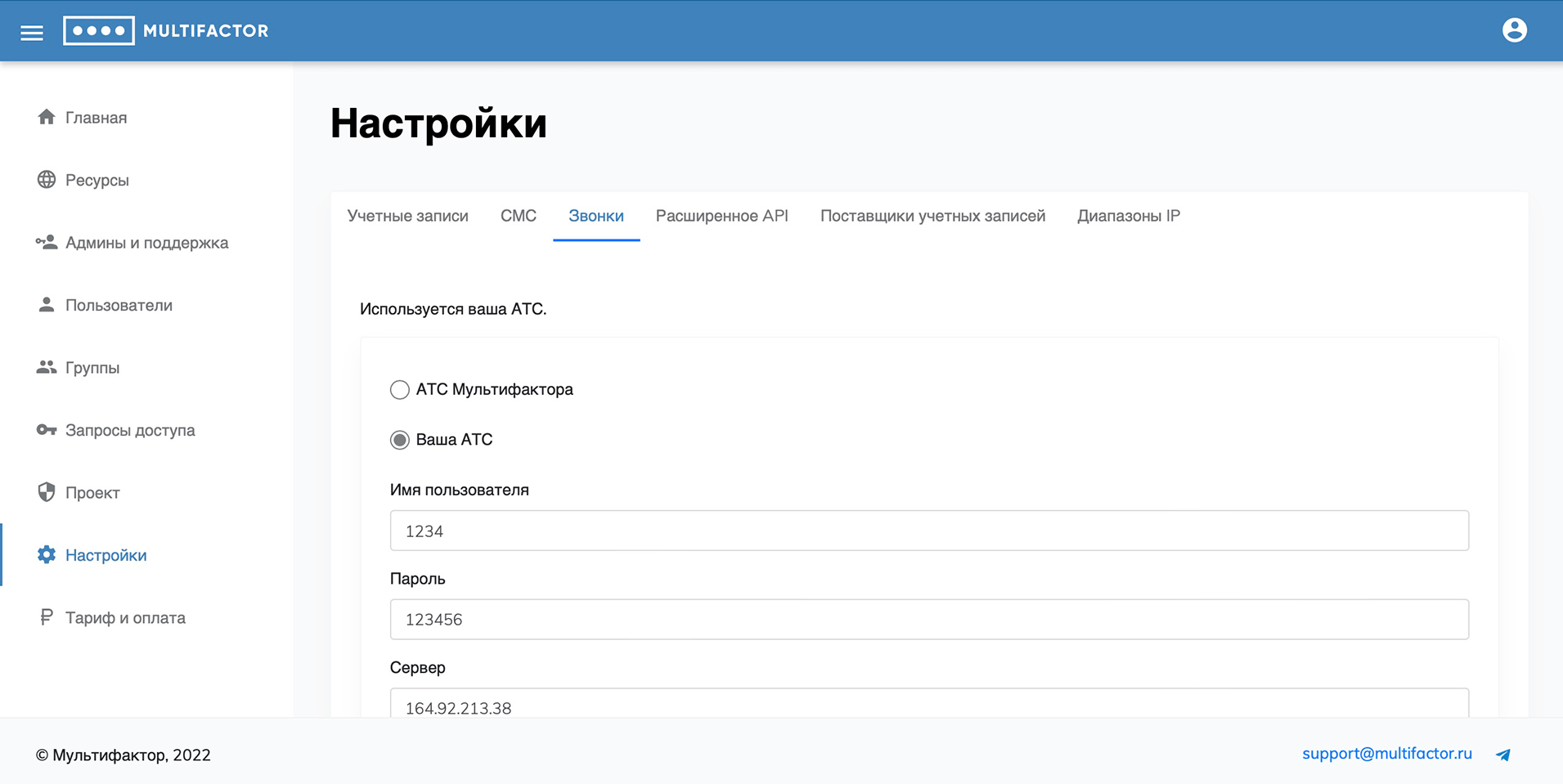
Calls
By default, Multifactor's ATS is used. It is possible to integrate using the SIP protocol. The work has been tested with Asterisk PBX (FreeBPX).
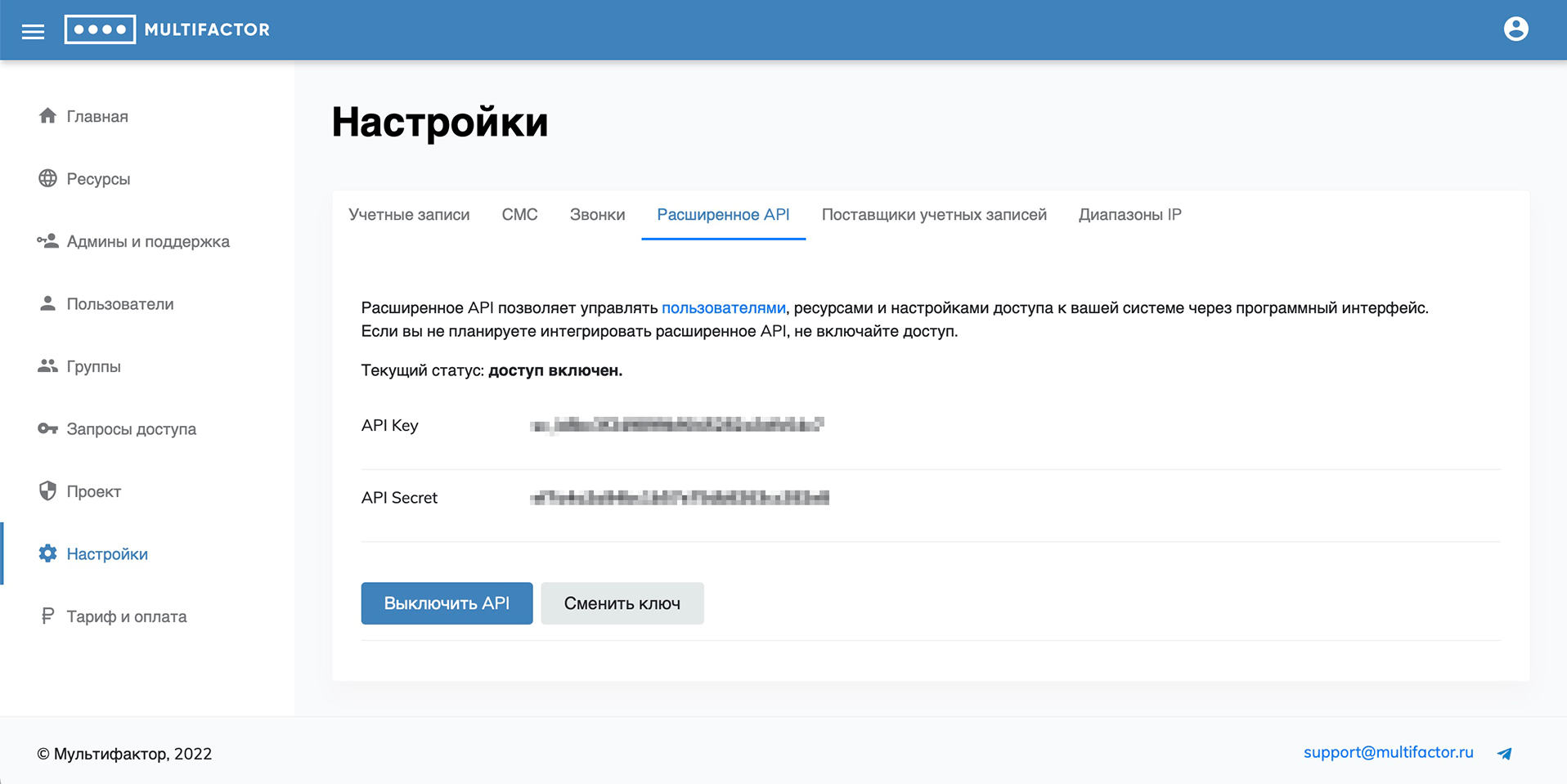
Extended API
The advanced API allows you to manage users, resources, and access settings for your system through a software interface. If you don't plan to integrate the extended API, don't enable access.
Also in our knowledge base there are instructions on API for managing users (access subjects) and API for managing resources (access objects).
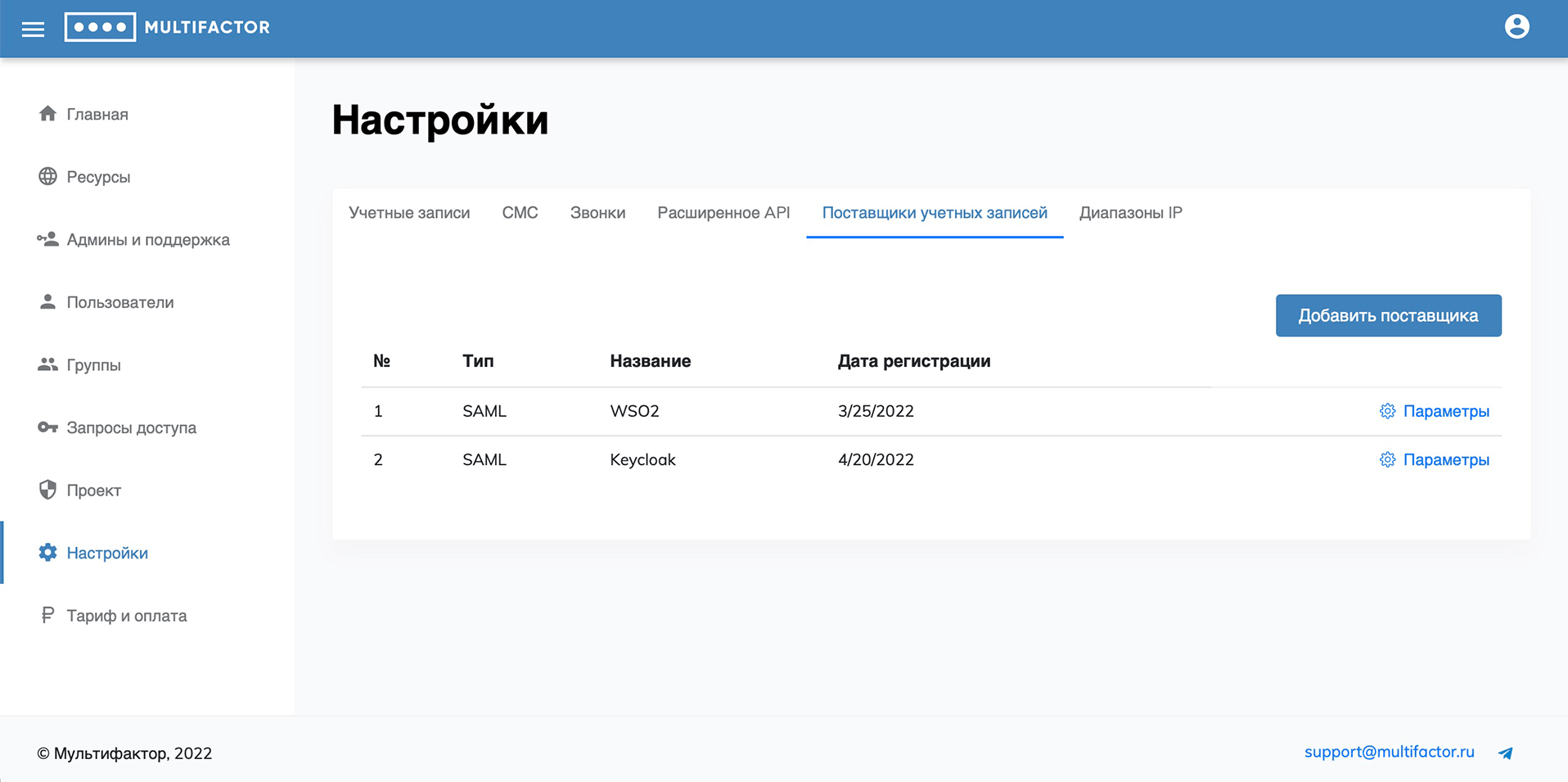
Account Providers
In this tab, you can add and configure SAML account providers for their subsequent use in SAML and OpenID-Connect resources.
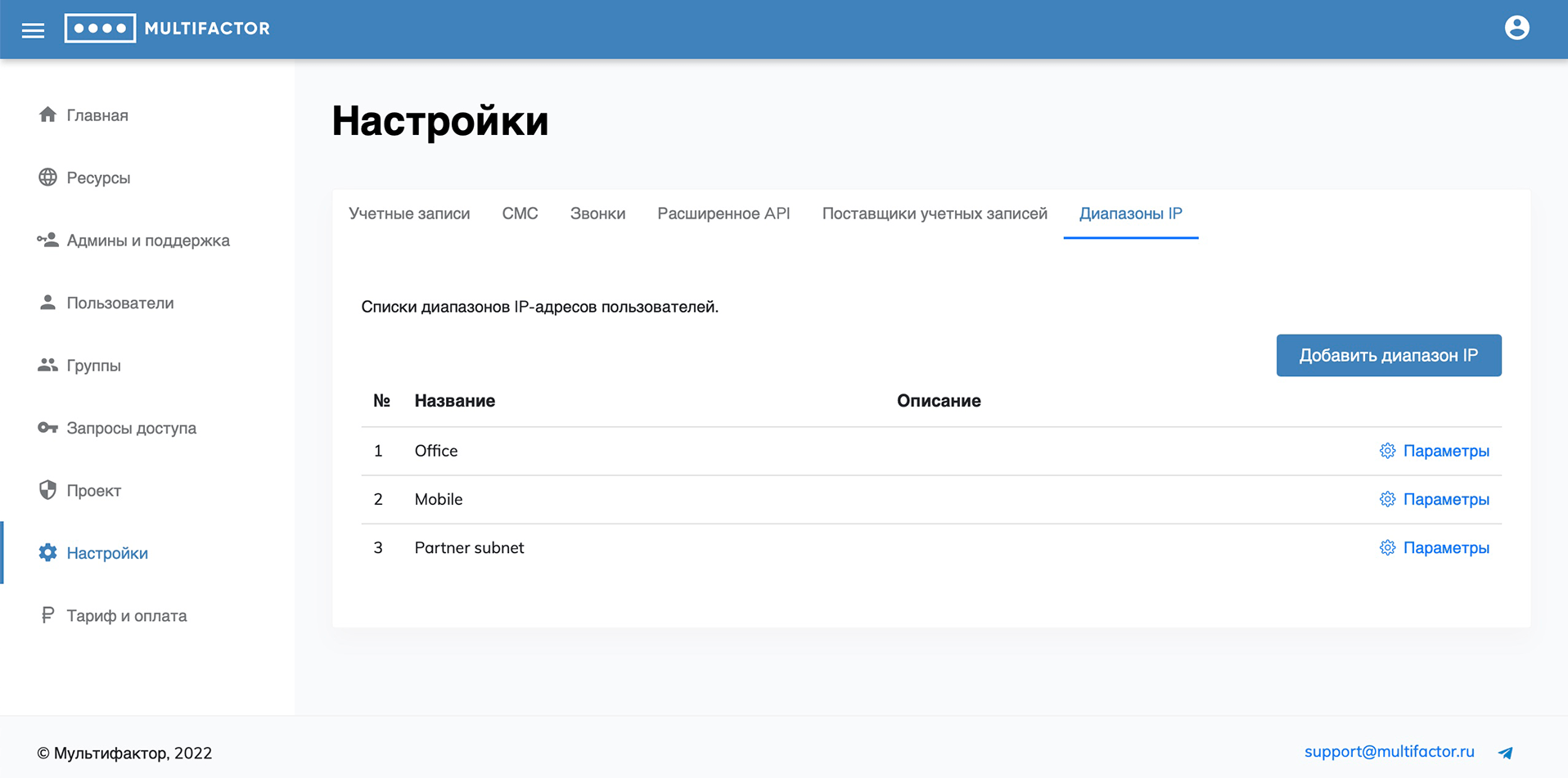
IP ranges
This tab specifies IP ranges for use in group policies to control the second factor request based on the IP user.
Magazine
This tab displays the actions of administrators. It displays the following actions:
- Login to the admin panel
- Deleting\Creating\Changing a resource
- Delete\Create\Change group
- Removing\Adding\Changing an employee
- Delete\Create\Change the list of IP addresses
- Changing the format of account names
- Start renaming accounts / removing duplicates
- Display the resource secret
- Enable\Disable API
- Change API secret
- Display API secret
- Sending a link to set up 2FA
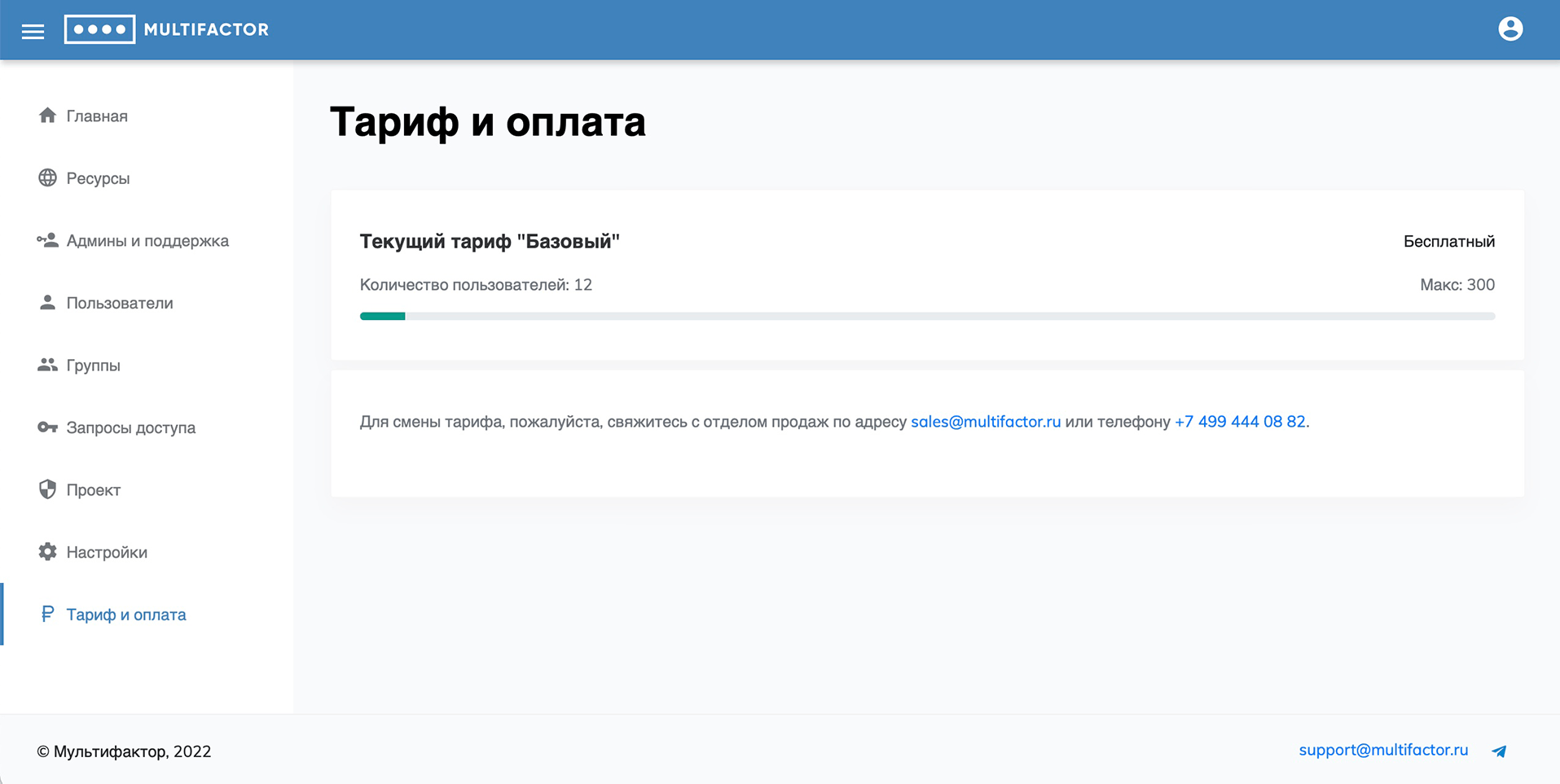
Tariff and payment
This section displays information about the current tariff, the number of available and used licenses.
The MULTIFACTOR two-factor authentication system is available free of charge for up to 3 users (inclusive).