Multifactor capabilities
Solution overview
A tool for reliable 2FA authentication of your users with a second factor when accessing any corporate resources (VPN, VDI, Windows and Linux infrastructure, cloud applications) with support for Single Sign-On (SSO) technology.
Simple, lightweight, requiring no additional capital expenditures on infrastructure and licenses from third-party vendors, a hybrid solution.

Quickly complete the project to implement Multifactor authentication in the organization (at least 2 hours), conduct automatic onboarding of employees, and realize the benefits on the same day:
- Additional level of security on top of the primary authentication method;
- Convenient access for external users to corporate resources without compromising security, continuity, and integrity of business processes;
- Optimization of costs for IT support and access management processes.
Platform components
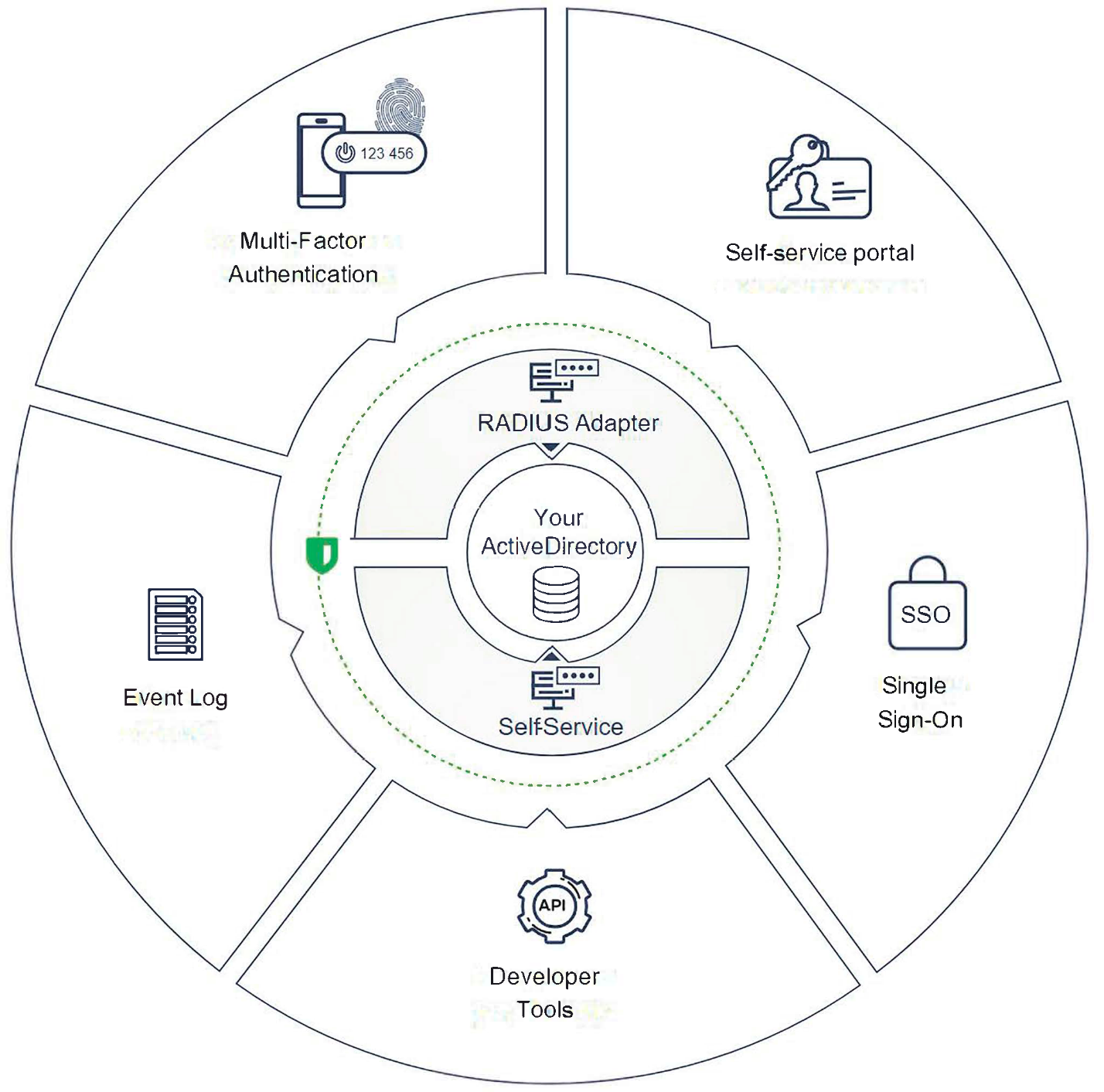
1. Multi-factor authentication and access control (MFA)
A tool for reliable user authentication ensuring access security to the company's information resources and network infrastructure. Reduces the risk of unauthorized access by 99%, without creating new risks. Prevents account hijacking, data leaks, and network attacks. Protects any resource, regardless of type or deployment.
Protect resources:
- Switching equipment, hardware and software firewalls (Check Point, Cisco, UserGate, Citrix Gateway, etc.);
- Cloud virtualization tools (VMware vCloud, Huawei Cloud, etc.);
- Remote workstations and VDI (Citrix, RDP, VMware Horizon, etc.);
- Cloud applications (GSuite, Trello, SalesForce, Slack, etc.);
- Windows infrastructure (Outlook Web Access, Windows VPN, NPS, Remote Desktop Gateway, etc.);
- Linux infrastructure (OpenVPN, SSH, Sudo, etc.).
Configure group access policies:
- Authentication methods;
- Information resources and access objects;
- Access restriction by IP address or range of addresses;
- Access restriction by days of the week and time.
1.1. Available authentication methods
MULTIFACTOR provides several different authentication methods that are available depending on the type of protected resource.

You, as the website administrator, configure the available options, while your users choose the most convenient ones for themselves.
2. Single Sign-On (SSO)
Allows you to combine user accounts from all corporate systems and popular cloud applications (Trello, Slack, SalesForce, etc.) under a single account provider (for example, Active Directory).
- Eliminates the multiplication of credentials;
- Reduces IT support costs;
- Increases the level of compliance with internal security policies and regulatory requirements.
3. Self Service Portal (SSP)
Allows the user to independently configure and confirm ownership of the second access factor, change the current or expired password after full authentication.
- Independent user onboarding;
- Self-configuration 2FA;
- Solving access problems without IT support.
4. Audit trail and notifications
All authentication transactions are logged and accessible through the administrator's dashboard. The log is invaluable for incident investigation and forensics.
The system notifies the system administrator of anomalies:
- Login from a new device;
- Simultaneous login from different IP addresses;
- Unsuccessful login attempts.
5. Administrator Dashboard
In the MULTIFACTOR administrator dashboard, you can manage users, user groups, resources, access objects, and authentication methods.
6. Developer Tools - REST API
Integrate Multifactor two-factor authentication with your proprietary applications and server infrastructure:
- Authentication in the Multifactor system;
- Creating access requests for two-factor authentication;
- User management (registration, changing user data, deleting);
- Generating a link to the interface for self-registration of the second factor by the user;
- Sending a link for self-registration to the user’s email.
Detailed documentation of the REST API.
Value proposition
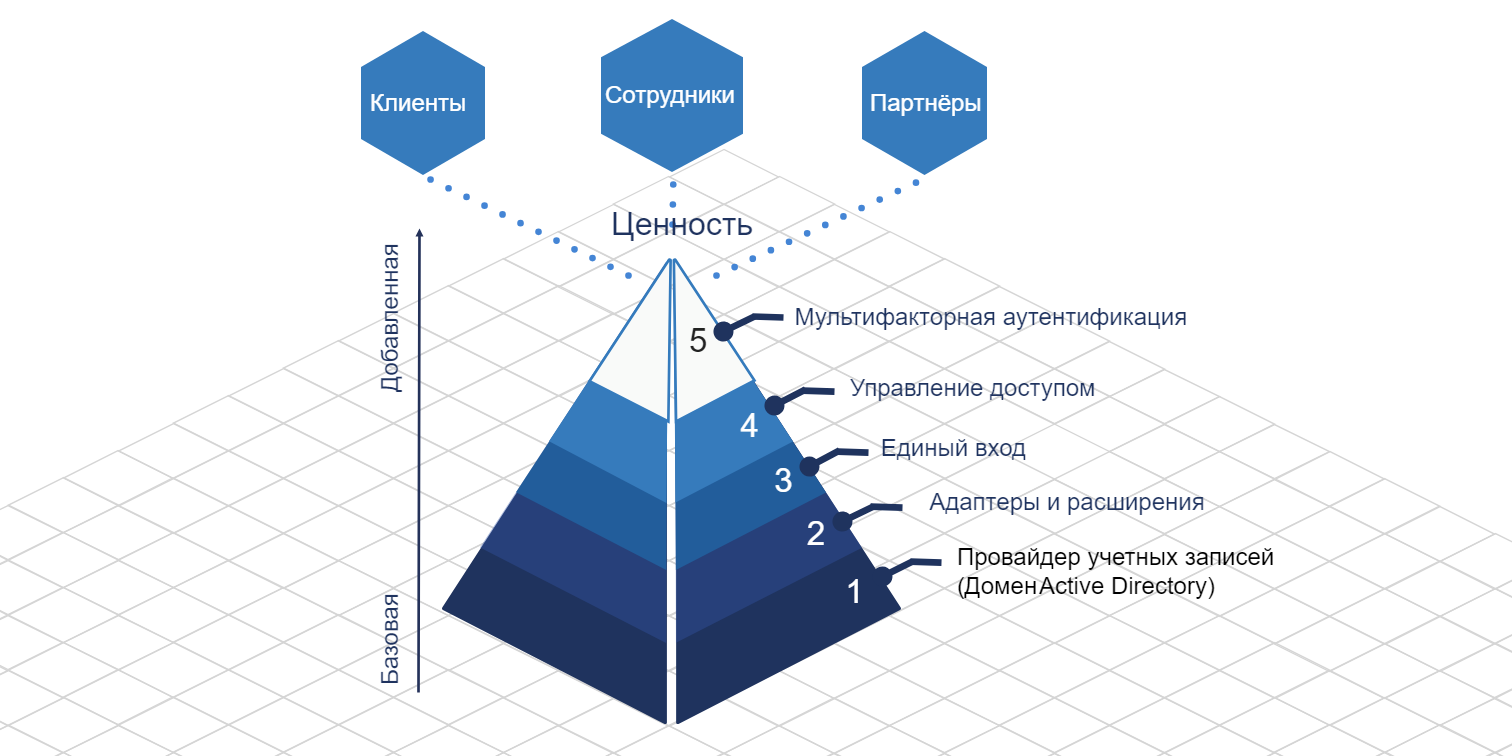
We create value both for the company as a whole and for all its stakeholders, from employees to management and partners.
Employees
Employees receive a convenient tool that allows them to remain productive. Unlike hardware tokens, which users may not see much value in and which can be easily forgotten or lost, the mobile phone with the authentication app is always at hand.
Management
Management receives a tool to ensure business process continuity and integrity; reduce IT support costs; optimize reserves for cyber risk; ensure security of critical entry points into the infrastructure. Builds trust with partners and regulators to ensure long-term business sustainability.
CEO
- Building trust with various parties: clients, partners, investors, consumers, regulators;
- Increasing business sustainability.
CFO
- Affordable solution for cyber risk management;
- Optimization of reserves for cyber risk;
- Protection of critical information.
COO
- Continuity of work processes;
- Coordination of access provision;
- Managing the process of hiring and firing employees.
CSO
- Security of entry points into the infrastructure;
- Increasing barriers to attackers;
- Organization of remote work security;
- Optimization of security audits.
Integration
Typical integration requires installation of our agents into the internal network perimeter of the company. Agents are distributed under an open source license, which makes sure that there are no undocumented features:
After installing the agents, you need to configure resources and access objects to work with MULTIFACTOR. Setup instructions are posted in our knowledge base.
Second factor authentication works through our MFA authentication center, located in the Dataline data center.