Two-factor authentication with Telegram bot setup for OpenVPN
This article describes an OpenVPN server setup for two-factor authentication activation via Telegram.
OpenVPN — is well-known, free of charge open-source server, which is used throughout to provide secured access for employees to the company's internal resources.
To verify the authenticity for the VPN server connection, as a rule, it is used the combination of key and user login/password. Herewith, a password saved on a client transfers all the set in a single factor which does not provide adequate security level. The intruder obtained access to the client computer, gains access to the VPN server as well. Especially it concerns the connections from the devices under Windows control.
Usage of the second factor reduces the risk of unauthorized access by 99% and principally does not make the process of users' connection process complicated.
Operation principle
- OpenVPN uses plugin openvpn-plugin-auth-pam for authentication verification.
- The plugin checks the user's password on the server and requests the second factor via RADIUS protocol in Multifactor service.
- Multifactor sends a message via Telegram Bot to the user with the request of access confirmation.
- The user confirms the access request in the Telegram chat and connects to VPN.
OpenVPN server setup
There are a lot of articles on the Internet describing the process of OpenVPN installation and setup, for this reason, we will not duplicate it. If you need help, there are some links to educational materials at the end of the article.
Multifactor Configure
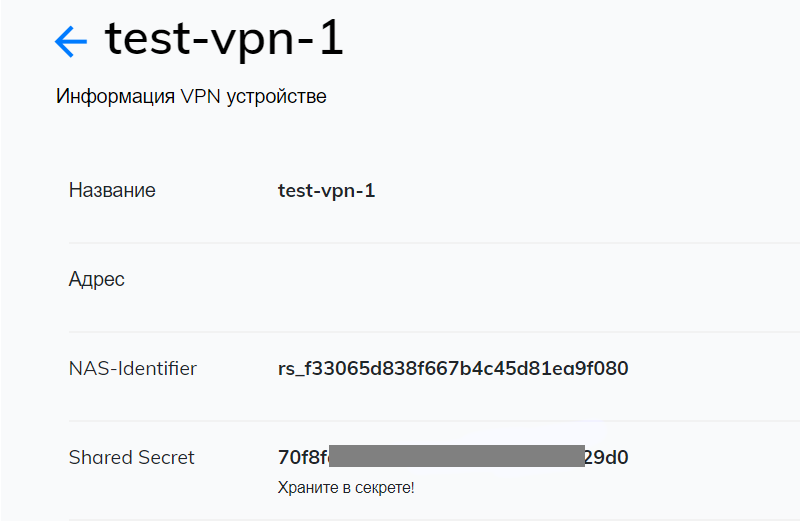
- Login the Multifactor admin panel, browse to section "Resources" and create new VPN. After VPN creation there will be available two parameters: NAS-IDentifier and Shared Secret, which are required for further settings.
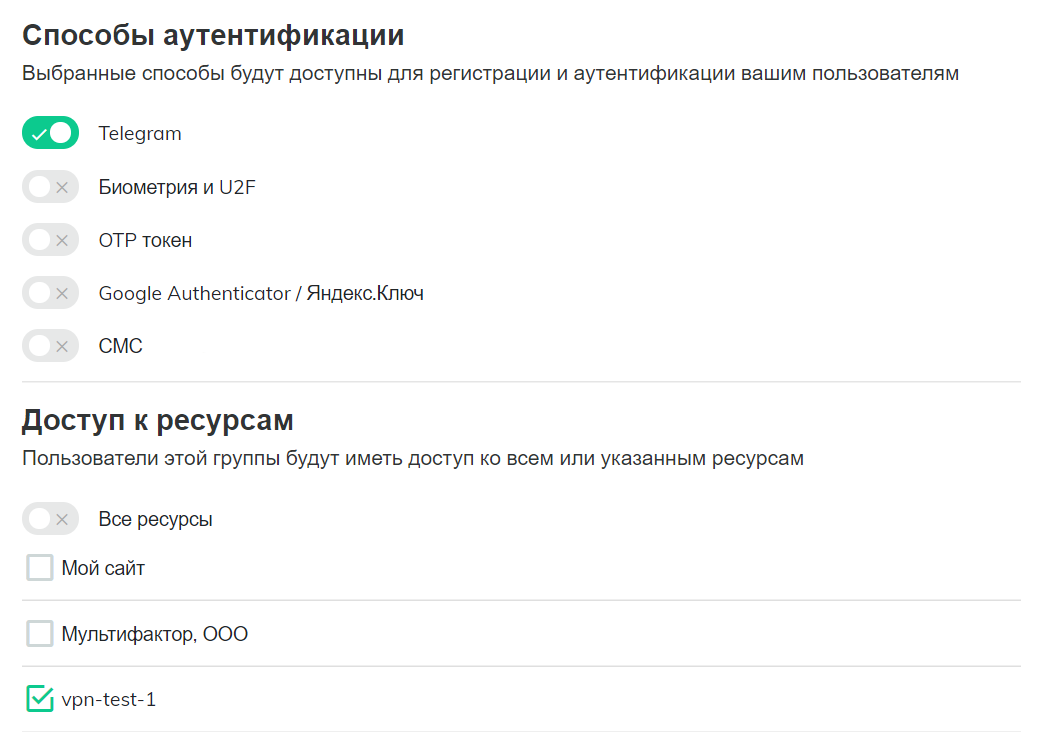
- In section "Groups" browse to group parameters "All users" and clear flag "All resources" in order to allow VPN server connection for the users of the definite group only.
- Create a new group "VPN users", uncheck all methods of authentication except Telegram, and make settings that all users have access to the created VPN resource.
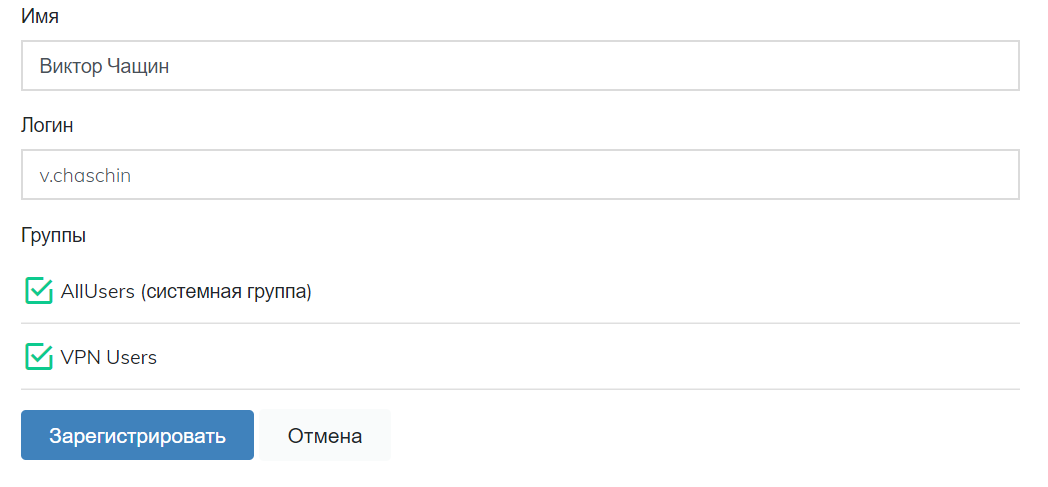
- In section "Users" create the users who should have access to VPN, add them in group "VPN users" and send a link for setting the second authentication method. User login and login on the VPN server shall be identical.
OpenVPN Server Configure
Open file /etc/openvpn/server.conf and add plugin for authentication by means of PAM module
plugin /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so openvpn
Plugin can be found in directory /usr/lib/openvpn/plugins/ or /usr/lib64/openvpn/plugins/ in dependence of your system.
Create a file for service-type openvpn
$ sudo vi /etc/pam.d/openvpn
and write in it
auth required pam_radius_auth.so skip_passwd client_id=[NAS-IDentifier]
auth substack password-auth
account substack password-auth
the first line connects PAM module pam_radius_auth with the parameters:
- skip_passwd — cancels the user's password transferring into Multifactor RADIUS server
- client_id — enter instead of [NAS-Identifier] the corresponding parameter from VPN resource settings Multifactor. All possible parameters are described in the module documentation.
The second and third lines activate system validation of login, password and user rights on your server together with the second authentication factor.
Thereafter it is necessary to install module pam_radius_auth
$ sudo yum install pam_radius
Open for editing the file /etc/pam_radius.conf and enter an address of Multifactor RADIUS server
radius.multifactor.ru shared_secret 40
where:
- radius.multifactor.ru — server address
- shared_secret — copy from the corresponding parameter of VPN resource settings Multifactor
- 40 — request timeout
all the other servers shall be deleted and commented out (put a semicolon at the start of the line)
Restart OpenVPN
$ sudo systemctl restart openvpn@server
Client Configure
Include in the client configuration file the request of user login and password
auth-user-pass
Validation
Start the client for OpenVPN, connect to the server, enter login and password. You'll receive an access request with two buttons from the Telegram Multifactor Bot.
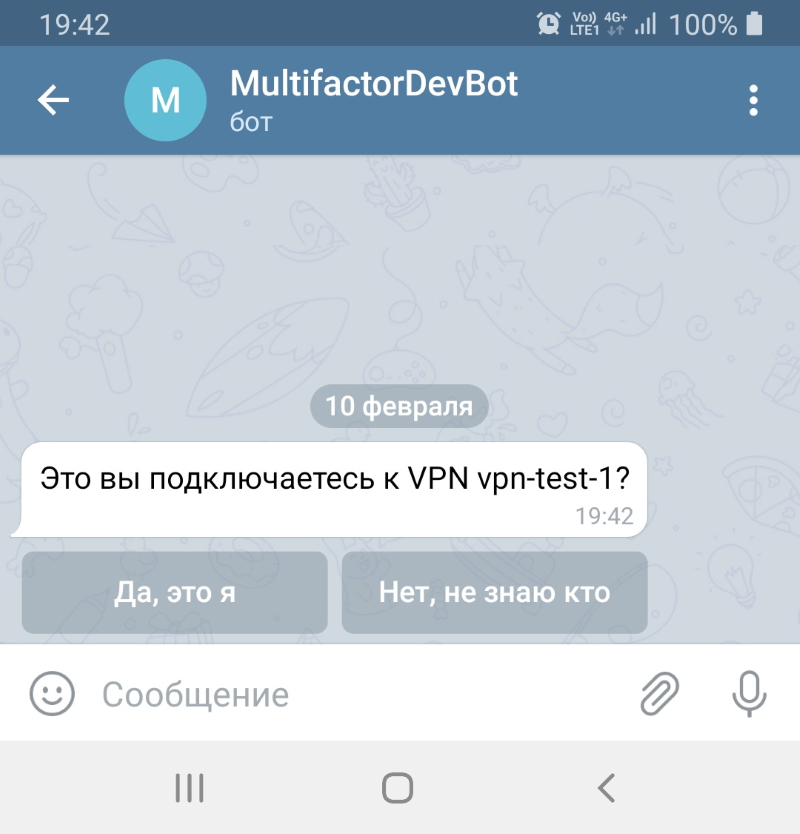
One button allows access, the other one blocks it.
Now you can save the password on the client, the second factor shall secure your OpenVPN server from unauthorized access.
If anything does not operate
Check sequentially if you miss anything:
- There is a user with the set password on the server with OpenVPN
- There is an UDP open access from the server for 1812 port to the address radius.multifactor.ru
- Parameters NAS-Identifier and Shared Secret are correct
- There is a user with the same login in Multifactor system and this user has access to VPN users group
- The user set an authentication method via Telegram
If nothing operates, please contact us for help.
Also, please see the following:
